Overview
This guide provides IT administrators with the required steps to integrate Avaya Aura Application Enablement Services (AES) 10.2 with Tenfold Cloud Connect (TCC). The integration enables Computer Telephony Integration (CTI) for real-time call event handling across various CRMs.
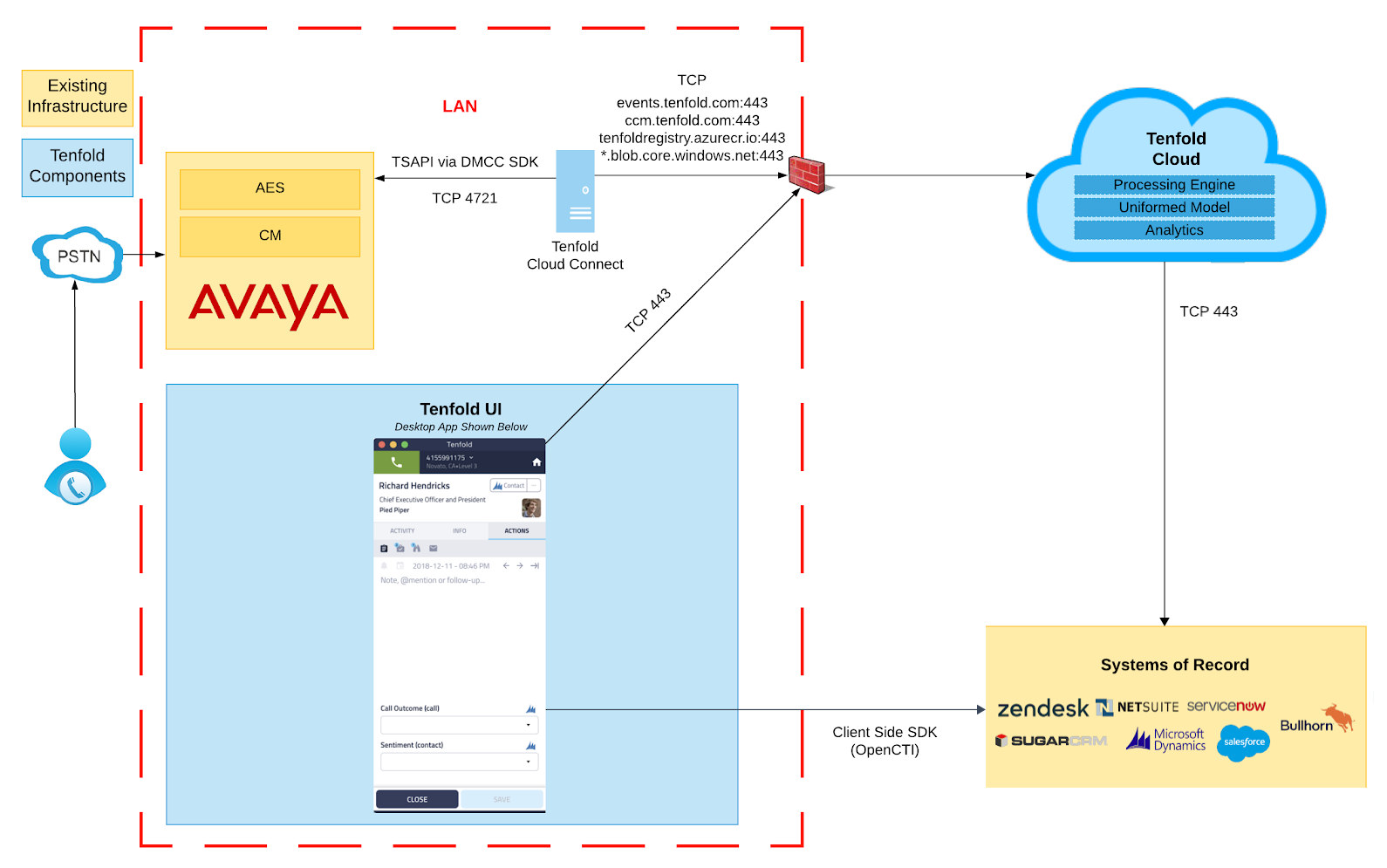
1. Integration Architecture
Components:
- Avaya Communication Manager (CM): Telephony control.
- Avaya AES 10.2: Provides TSAPI and DMCC interfaces.
- Tenfold Cloud Connect (TCC): On-premise bridge to Tenfold Cloud.
- Tenfold Cloud: Processes CTI events and interacts with CRM.
+---------------------+ TCP 4721/4722 +----------------------+ HTTPS +----------------+| Avaya Communication| <--------------------------> | Avaya AES 10.2 | <---------------> | Tenfold Cloud || Manager | | | | |+---------------------+ +----------------------+ +----------------+ ^ | | | LAN/DMZ | | v | +----------------------+ | Tenfold Cloud Connect | | (On-Premises Linux) | +----------------------+
2. System Requirements
Avaya Components
- AES Version: 10.2 or later
- CM Version: 10.1 or later
Tenfold Cloud Connect Server
- OS:
- Ubuntu Server 18.04 LTS or later
- Windows Server 2016/2019 with Desktop Experience
- Hardware:
- Quad-core CPU, 2.3 GHz+
- 16 GB RAM
- 250 GB free disk (7200 RPM or SSD)
- Gigabit Ethernet
- Network Access:
- Outbound HTTPS (443):
ccm.tenfold.com, events.tenfold.com, downloads.tenfold.com - ICMP must be allowed from TCC
- TCP Port 4721 or 4722 open bidirectionally to AES
3. Licensing Requirements
- TSAPI Basic User License: One per monitored agent/extension
- DMCC License: One per TCC instance (not per agent)
- CTI Link: Must be licensed and enabled on CM
- AES TSAPI Configuration:
- Admin role for TSAPI user
- Stream names for geo-redundancy
4. Prerequisites
- Complete the "TCC x Avaya AES Prerequisites" checklist.
- Confirm AES is reachable via TCP (4721/4722) from TCC.
- Verify AES certificates if TLS is enforced.
5. AES Configuration Steps
Step 1: Create CTI User
- Log into AES Web GUI
- Go to User Management > Add User
- Set User Role to: TSAPI User
- Assign to cti_provisioned_apps group
Step 2: Add CTI Link
- Log into Avaya CM SAT
- Run
add cti-link x - Type: ADJ-IP; Name: TCCLink
- Link Number: (choose available number)
Step 3: Add Switch Connection in AES
- Go to Communication Manager Interface > Switch Connections
- Add CM Switch Name
- Enable DMCC, TSAPI, and JTAPI services
Step 4: Enable DMCC Security Profile (if needed)
- Navigate to Security > DMCC Configuration
- Allow device control and monitoring
6. TCC Installation Steps
Linux
- SSH into server
- Run:
curl -O https://downloads.tenfold.com/app/tcc/install.shchmod +x install.shsudo ./install.sh
- Follow prompts to enter AES connection info, TSAPI credentials, and feature access codes.
Windows
- Download installer from
downloads.tenfold.com - Run as Administrator
- Complete configuration wizard with AES and CM credentials
7. Verification & Testing
Run the following from the TCC host:
curl https://events.tenfold.com/ping # Expect: pongcurl https://ccm.tenfold.com/ping # Expect: pongtelnet <AES_IP> 4721 # Expect: connected cursor
Verify from the Tenfold Admin Portal that:
- Agents appear online
- Events are flowing to CRM
8. Known Issues & Recommendations
- No SIP agent support
- No PSTN transfer/conference handling
- Restart
tcc.service after AES failover or CTI link drop - Use Avaya Agent for Desktop instead of One-X Communicator for accurate reason codes
- Avoid duplicate skill configuration across TCC instances
9. Support & Resources